Pkcs11-tool No Slot With A Token Was Found
Yhsm2-tool -sign -m SHA384-RSA-PKCS-PSS -id 0401 -i t3200.dat -o t3200.dat.sig-pss Using slot 0 with a present token (0x0) Logging in to 'YubiHSM'. Please enter User PIN: Using signature algorithm SHA384-RSA-PKCS-PSS PSS parameters: hashAlg=SHA384, mgf=MGF1-SHA384, saltlen=48. 1.1 Description of this Document. This PKCS #11 Cryptographic Token Interface Usage Guide Version 2.40 is intended to complement PKCS11-Base, PKCS11-Curr, PKCS11-Hist and PKCS11-Prof by providing guidance on how to implement the PKCS #11 interface most effectively. Airsoft International Magazine Forum - Member Profile Profile Page. User: Tf2 craft secondary slot token, tf2 craft slot token pda2, Title: New Member, About: Tf2 craft secondary slot token. Slots and Tokens ¶ A slot originally referred to a single card slot on a smartcard device that could accept a token. A token was a smartcard that contained secure, encrypted keys and certificates. You would insert your smartcard (token) into the slot, and use its contents to do cryptographic operations. Nowadays the distinction is more blurry. C: Program Files (x86) OpenSC Project OpenSC toolspkcs11-tool.exe -module eps2003csp11.dll -M No slot with a token was found. Share improve this answer edited Jul 30 '14 at 6:28.
As you may know, I'm trying to implement writing certificate to OpenPGP
card via PKCS#11.
 I succeed with pkcs15-init tool but have difficulty with pkcs11-tool.
I succeed with pkcs15-init tool but have difficulty with pkcs11-tool.When I import via pkcs15-init tool (Command: pkcs15-init
--store-certificate ***@mbm.vn.pem), the tool asks for Admin PIN
and the work is done. But when I try with pkcs11-tool:
pkcs11-tool --module=/usr/lib/opensc-pkcs11.so -w quannguyen.crt -y cert
--slot 2
the tool does not ask for PIN and the write cannot succeed (in OpenPGP
card, writing certificate requires SO (Admin) PIN).
I tried to provide the Admin PIN in the command, but still not successful:
pkcs11-tool --module=/usr/lib/opensc-pkcs11.so -w quannguyen.crt -y cert
--slot 2 -l --so-pin 12345678
pkcs11-tool --module=/usr/lib/opensc-pkcs11.so -w quannguyen.crt -y cert
--slot 2 --so-pin 12345678
I also researched and found that in pkcs15-init, a function to ask for
 PIN is implemented and added via sc_pkcs15init_set_callbacks(), but
PIN is implemented and added via sc_pkcs15init_set_callbacks(), butpkcs11-tool does not do so.
The question is:
- 'Not ask for PIN' is intentional design of pkcs11-tool or a limitation?
- What is the right way to provide Admin PIN to pkcs11-tool to allow to
write data?
Pkcs11-tool No Slot With A Token Was Found Inside
- When I do import certificate in Firefox, the browser ask for a PIN. Iexpect it to ask for Admin PIN but not sure which PIN it actually asks
for (user PIN, to login to slot, or admin PIN, to write data). Do you
know how Firefox determines which PIN to ask? Does it always ask for
user PIN of the slot, or smart enough to ask for right PIN?
Regards,
Quân
pkcs11-tool: utility for managing and using PKCS #11 security tokens
Command to display pkcs11-tool manual in Linux: $ man 1 pkcs11-tool
NAME
pkcs11-tool - utility for managing and using PKCS #11 security tokens
SYNOPSIS
pkcs11-tool[OPTIONS]
DESCRIPTION
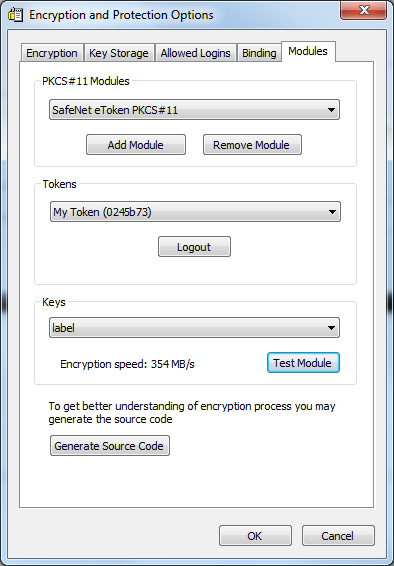
Thepkcs11-toolutility is used to manage the data objects on smart cards and similar PKCS #11 security tokens. Users can list and read PINs, keys and certificates stored on the token. User PIN authentication is performed for those operations that require it.
OPTIONS
--login, -l
- Use the givenpinas the Security Officer PIN for some token operations (token initialization, user PIN initialization, etc). The same warning as--pinalso applies here.
--init-token
- Initializes the user PIN. This option differs from --change-pin in that it sets the user PIN for the first time. Once set, the user PIN can be changed using--change-pin.
--change-pin, -c
- Performs some tests on the token. This option is most useful when used with either--loginor--pin.
--show-info, -I
- Displays a list of available slots on the token.
--list-mechanisms, -M
- Displays a list of objects.
--sign, s
- Use the specifiedmechanismfor token operations. See-Mfor a list of mechanisms supported by your token.
- Write a key or certificate object to the token.
- Specify the id of the object to operate on.
- Specify the id of the slot to use.
- Set the CKA_ID of the object.
- Specify the path to a file for input.
- Specify a PKCS#11 module (or library) to load.
- Causespkcs11-toolto be more verbose. Specify this flag several times to enable debug output in the OpenSC library.
- pkcs11_eventmgr (1) - SmartCard PKCS#11 Event Manager
- pkcs11_inspect (1) - print certificate contents
- pkcs11_listcerts (1) - SmartCard PKCS#11 certificates listing
- pkcs11_setup (1) - SmartCard PKCS#11 setup
- pkcs15-crypt (1) - perform crypto operations using pkcs15 smart card
- pkcs15-init (1) - smart card personalization utility
- pkcs15-tool (1) - utility for manipulating PKCS #15 data structures on smart cards and similar security tokens
- pkcsconf (1) - configuration utility for the pkcsslotd daemon
--hash, -h
--keypairgen, -k
--typetype, -ytype
--labelname, -aname
--slot-idname
--attr-frompath
--output-filepath, -opath
Pkcs11-tool No Slot With A Token Was Found Within
--moz-certpath, -zpath
SEE ALSO
opensc(7)